If you believe your security questions are a solid backup for your passwords, you might be in for a surprise. Hackers have clever ways of uncovering those answers, and it is often easier than you think.

Social media is a goldmine for anyone trying to piece together your personal story—and hackers know it. Most people casually share key life events online, like birthdays, anniversaries, pets’ names, and schools. However, to someone trying to crack your security questions, that is not nostalgia. That is intel.
Say your security question is “What is your favorite movie?” Two scrolls through your X account reveal your undying love for The Lion King. Or maybe your Instagram bio says “Dog mom to Max,” and there is your answer to “What was your first pet’s name?”

Related
Here’s How Scammers Can Take Advantage of Your Social Media Profile
Knowing their ways is the first step!
This kind of snooping does not require fancy tools. All a hacker needs is your name, your profile, and a little patience. They will dig through old posts, tagged photos, and even the comments your friends leave. If your privacy settings are wide open, you’re essentially handing over the answers.
Even private accounts are not safe. If a hacker manages to follow you, maybe through a fake profile, your posts become accessible. A harmless memory lane post can turn into a breadcrumb trail right to your accounts.
7
Using Fake “Fun” Quizzes
Chances are, you’ve seen a version of those playful quizzes on social media asking things like, “What is your royal name?” or “Can we guess your age based on your favorite foods?” They are usually framed as harmless fun, but they are one of the most common privacy blunders you can make on social media.
Hackers, or at least shady data scrapers, use these quizzes to collect the exact kind of personal details often tied to security questions. They lower your guard with humor and personalization so you forget you are essentially handing over a map to your digital identity.
6
Looking Up Details in Public Records
Sometimes hackers do not need tricks at all. They just use public records.
Marriage certificates, property records, voter registrations, and even old yearbooks can be rich sources of answers to security questions. Information like your mother’s maiden name, childhood address, or birthplace is often just a few searches away.

Related
How to Delete Your Personal Data From Public Record Websites
Don’t want your information falling into the wrong hands? Learn how to delete your personal information from the web!
For example, if your security question is “What city were you born in?”, an old birth announcement could easily reveal it. Similarly, a marriage license could expose a father’s middle name.
A determined hacker does not even need to know you personally. They just need your name and a little persistence. Public records can fill in the rest.
5
Searching Through Old Forum Posts
You might think old forum posts are safe because most forums were anonymous. But hackers know anonymity isn’t bulletproof—especially when people accidentally leave a trail.
Maybe you used a forum handle that matches part of your email address. Maybe you posted about your hometown, your first pet, or your high school mascot. Even tiny details like the year you graduated or your favorite sports team can start connecting the dots back to you.
It doesn’t take hacking skills, either. A hacker with patience can search old forums, cross-reference usernames, or Google a few keywords alongside your name. Forums you barely remember joining might still have public archives floating around, quietly leaking bits of your personal history.
Anonymity helps, but if you left enough breadcrumbs, old posts can still betray you. And when hackers are hunting for answers to your security questions, even the smallest clue can be enough.
4
Using Leaked Data From Other Sites
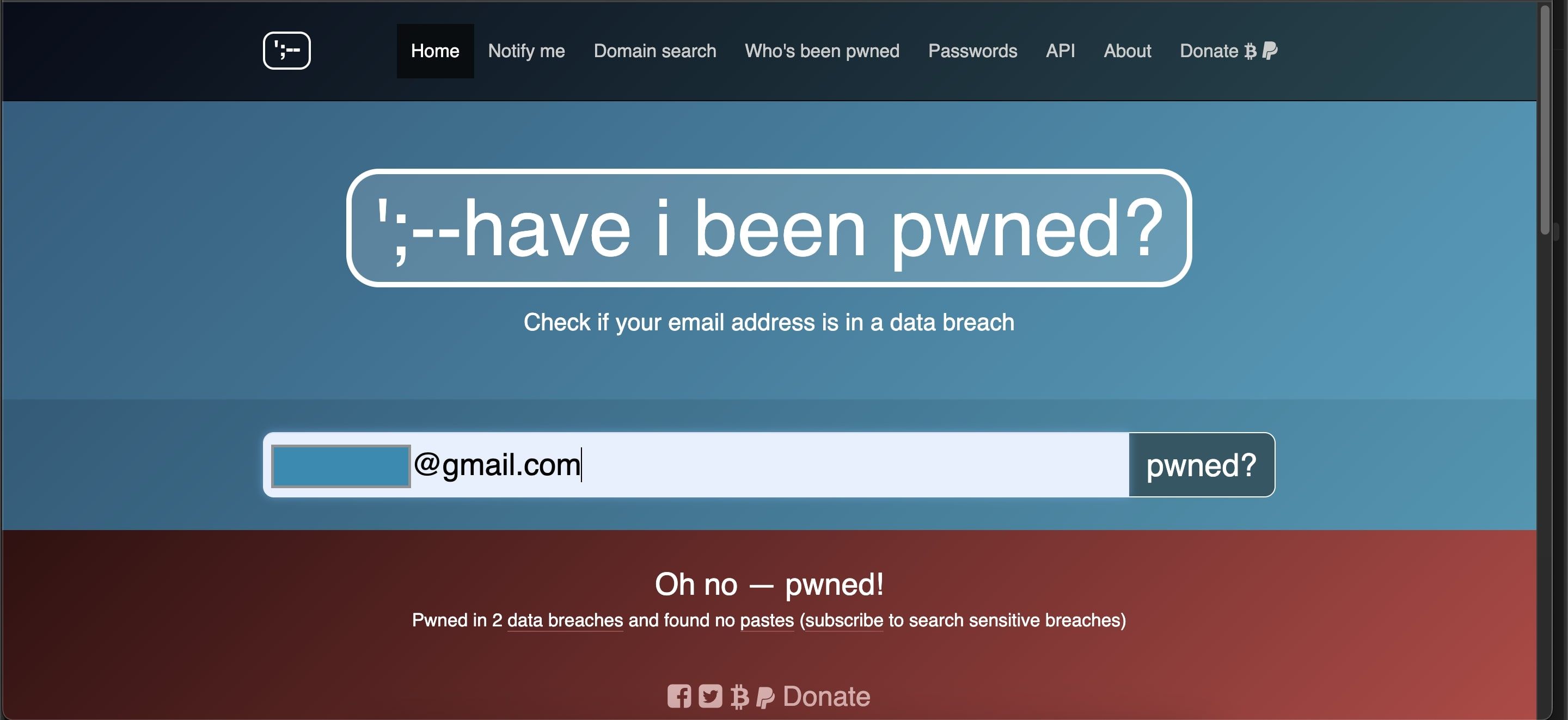
Data breaches are like jackpots for hackers. When a site gets hacked, it is not just usernames and passwords that get leaked. Sometimes your security question answers are leaked, too.
For example, say you set up an account on a forum years ago. You used “Arsenal” as the answer to “What is your favorite sports team?” and forgot about it. If that site is breached and your answers were not encrypted, hackers could use that to access your important accounts today.
Reusing security answers across sites is just as dangerous as reusing passwords. Once your info is out there, hackers use specialized tools to cross-reference it. Use a tool like Have I Been Pwned to see if your data’s been exposed. And always treat security answers like one-time-use passwords: unique for every account.
3
Creating Fake Support Chats
This one is more sophisticated but devastatingly effective: fake customer support chats.
It usually starts with an email, DM, or pop-up mimicking your bank, email provider, or favorite store. The fake support agent will ask you to confirm your identity by answering security questions.
These fake chats often copy branding, language, and even timing, for example, during a real site outage. And because they feel personal, you are more likely to comply quickly without thinking. Once you hand over those answers, hackers can gain access to your account by resetting your login credentials.

Related
How I Spot Fake Customer Support Scams Before They Fool Me
I can see through their schemes with a few tricks.
The golden rule here is simple. Legitimate support reps will never ask for your security questions via chat, email, or direct message. If you receive a request like that, close the chat and verify directly through the official site.
2
Tricking Your Friends Into Sharing Details
Hackers know that even if you are cautious, your friends might not be. It is surprisingly easy to get personal details by tricking people you trust.
Sometimes it starts with a fake profile pretending to be an old classmate or mutual friend. They slide into conversations, ask about “the good old days,” or start a game that feels harmless. Before your friend knows it, they have casually mentioned where you grew up, your childhood pet’s name, or even your favorite teacher.
Even something as simple as a nostalgic Facebook post can spill too much. A friend tagging you in an old yearbook photo or joking about your first car can give hackers exactly what they need, without you ever typing a word.
It is a sneaky tactic because it feels so natural. Friends trust each other. Hackers exploit that trust to do the digging for them. If you’re serious about security, remind your inner circle to be cautious too.
1
Guessing Common Answers
Sometimes, hackers do not even have to snoop. They just guess, and unfortunately, they are often right.
Questions like “What is your favorite color?” lead to predictable answers like blue. Pets’ names often involve Max, Bella, or Lucky. Even something like “mother’s maiden name” often leads to common last names like Smith, Johnson, or Garcia. Other answers are similarly predictable: A lot of people answer “dream vacation” with “Paris,” for example.
Hackers sometimes automate this guessing, cycling through the most popular answers until they get lucky. Without strong site protections like lockouts after wrong attempts, they might only need a few tries.
The takeaway is simple. Treat security question answers like passwords. Don’t go with the truth if the truth is too easy to guess. Make it a passphrase, something nonsensical, or better yet, use a password manager to store randomized answers.
Security questions might feel like harmless backups, but to a hacker, they are an unlocked side door. Hackers do not always need to break in with brute force. Sometimes they just walk in using the details you left lying around.








Leave a Comment
Your email address will not be published. Required fields are marked *