Ever feel like someone’s watching you through your laptop? If your device is acting strange, it might not be paranoia. Thankfully, there are some simple ways to spot hidden monitoring software and regain control of your privacy.
1
Look for Unusual Behavior
One of the first telltale signs that someone might have installed monitoring software on your laptop is a noticeable change in how it behaves. Using this same technique, you can spot malware on your smartphone.
Monitoring tools often run in the background, silently collecting data or logging your activity, which can strain your system and lead to unusual behavior. If your laptop feels sluggish, takes longer to boot up, drains the battery faster, or its fans are unusually loud even when you’re not running heavy applications, that could be a clue that something is off.
Pay attention to pop-ups, especially in strange locations, like when you’re not browsing, or an abnormal increase in pop-up ads across your favorite websites. Also, watch for frequent crashes that you can’t put a finger on or unexpected restarts.
If you often use your mobile hotspot to connect your laptop to the internet, an unexpected spike in data usage can be another red flag. Monitoring software can cause all of these issues. In short, trust your instincts. If your laptop feels off, it probably is.
2
Scan Your System for Malware
One trait of modern malware is that it’s stealthier than older counterparts, which makes detection much more challenging in typical ways, like random pop-ups showing up. Fortunately, many monitoring tools, especially keyloggers and spyware, are categorized as malicious software by reputable antivirus programs.
Using these programs, you can perform a full system scan to help detect and remove threats before they do more harm. Built-in security tools like Microsoft’s Windows Defender and Apple’s XProtect might not sound worth your time, but I recommend using them as your first line of defense.
Ensure your virus definitions are up to date, then perform a full scan rather than a quick one, as monitoring software can hide deep within system files.

Related
Is Windows Defender All the Antivirus Protection You Need?
Do you really need to download extra antivirus software if you have Windows Defender installed?
If you’re unsatisfied with the scan results, consider using a trusted third-party antivirus or anti-malware solution like Malwarebytes or Bitdefender. These tools often detect threats that default programs may miss.
Some even offer specific features for identifying keyloggers, rootkits, and remote access tools. But they don’t come for free or cheap. So, before committing, ensure the antivirus software has all the essential features.
3
Review Browser Extensions
Browser extensions can be useful, but can also be tools for spying on your activity. Malicious or rogue extensions can track browsing habits, display ads, log keystrokes, or even redirect you to fake websites to steal your information. That’s why reviewing your browser extensions is essential when checking for monitoring software.

Related
These 30 Chrome Extensions Were All Breached, and Millions of Users Are Affected
Double-check to make sure you’re not one of the millions of affected users.
Go through the list carefully and look for anything you don’t recognize or remember installing. Pay extra attention to extensions that claim to offer utility functions like security enhancement—these are sometimes used as disguises for spyware.
Also, check out our extensive list of Chrome extensions that look legit but spy on you, and ensure that none of the ones mentioned are installed. To stay safe, stick to well-reviewed and trusted extensions from reputable developers. Moving forward, check the safety of extensions before you install them in Chrome, Firefox, or any other browser.
4
Check Your Webcam & Microphone Access
One of the more unsettling ways someone could monitor you is by secretly accessing your laptop’s webcam or microphone. Because of this, you should regularly review which apps have access to your webcam and microphone.
On Windows 11, click the Windows icon, go to Settings > Privacy & Security, then scroll down to App permissions. From the list, select Camera or Microphone and scroll down the page to see which applications have permission for the selected sensor.
On macOS, navigate to System Settings > Privacy & Security, then select Camera or Microphone from the list.
While on the respective pages, look for any apps you don’t recognize or didn’t intentionally grant access to. If unsure, turn off the app and watch if anything breaks.
Another way to tell you’re being monitored is when your webcam light turns on randomly without input. However, that may not always be the case since some sophisticated monitoring software can turn off the indicator light while recording you, making detection harder.
5
Check Your Installed Programs
Often, monitoring software disguises itself as a harmless or obscure application, hoping to blend in with legitimate programs. These apps may even install additional apps in the background without your knowledge. That’s why periodically reviewing all installed software on your laptop is essential, especially if you suspect someone may have tampered with your device.
On Windows 11, open Settings and navigate to Apps > Installed apps to view a list of your installed applications.
On macOS, open the Applications folder or navigate to System Settings > General > Storage > Applications to get a similar overview.
Go through the list individually and look for anything that seems unfamiliar, has a generic name, or was installed recently without your knowledge. If you’re unsure about a specific app, a simple online search for its name, developer, functionality, or reviews can help determine its legitimacy.
6
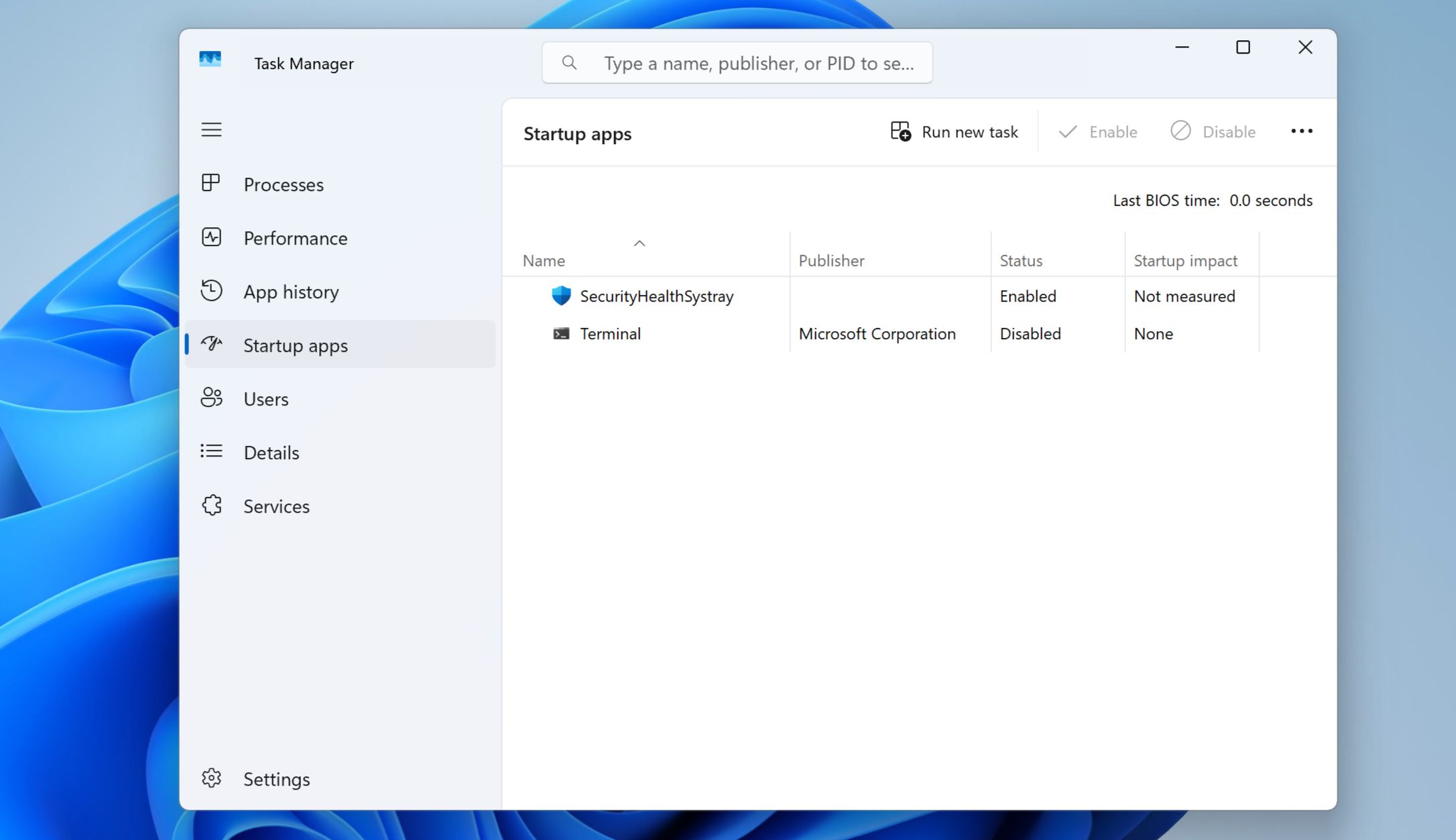
Review Startup Programs
Many types of monitoring software are designed to automatically launch when you start your laptop, so they can begin collecting data immediately without drawing attention to themselves. This is common even for employee monitoring software.
As such, reviewing your startup programs is a smart way to uncover hidden tools running in the background. On Windows 11, press Ctrl + Shift + Esc to open the Task Manager, then click Startup apps in the left sidebar. This shows a list of all programs set to launch when your system boots.
On macOS, go to System Settings > General > Login Items & Extensions to see a similar list.
7
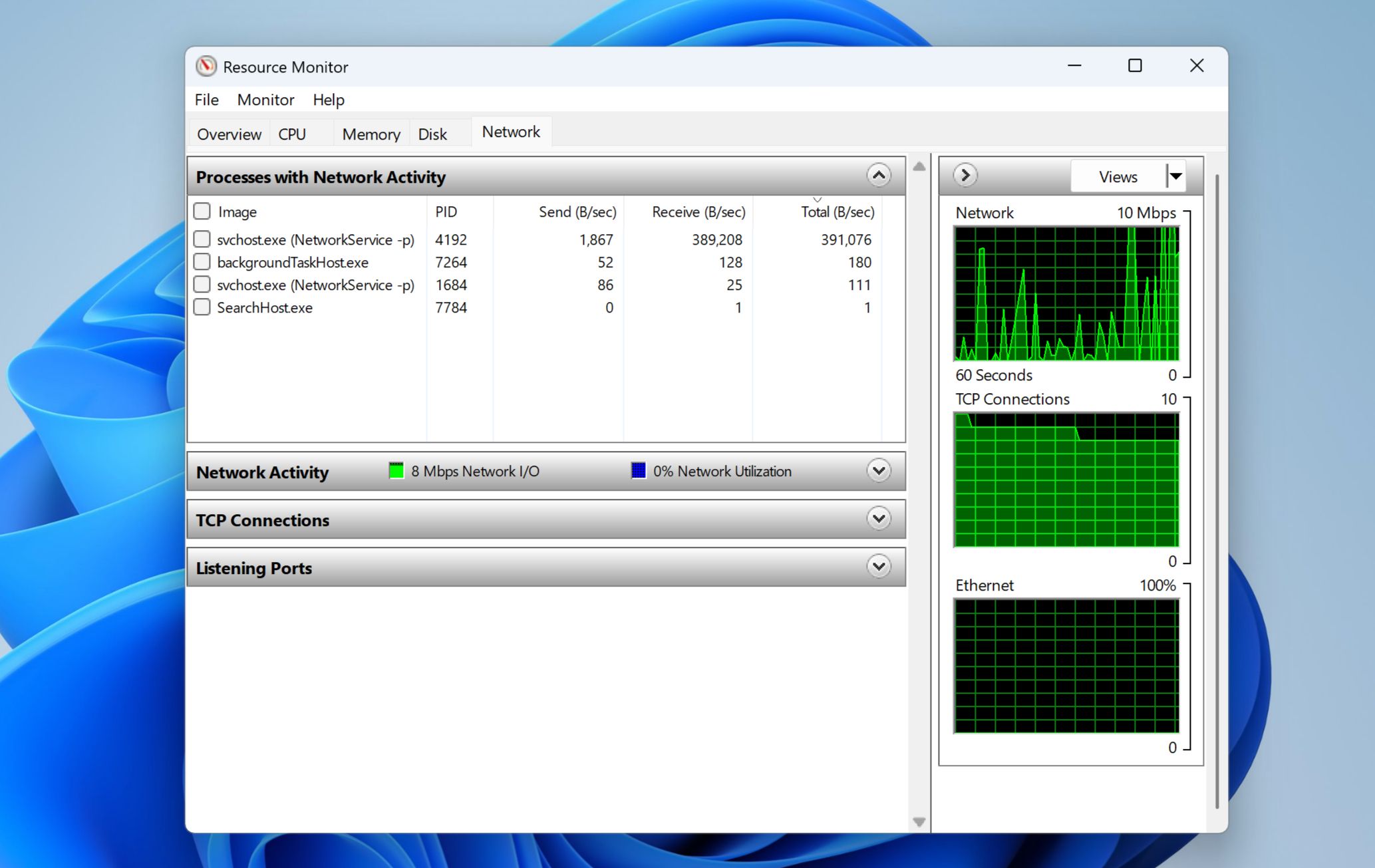
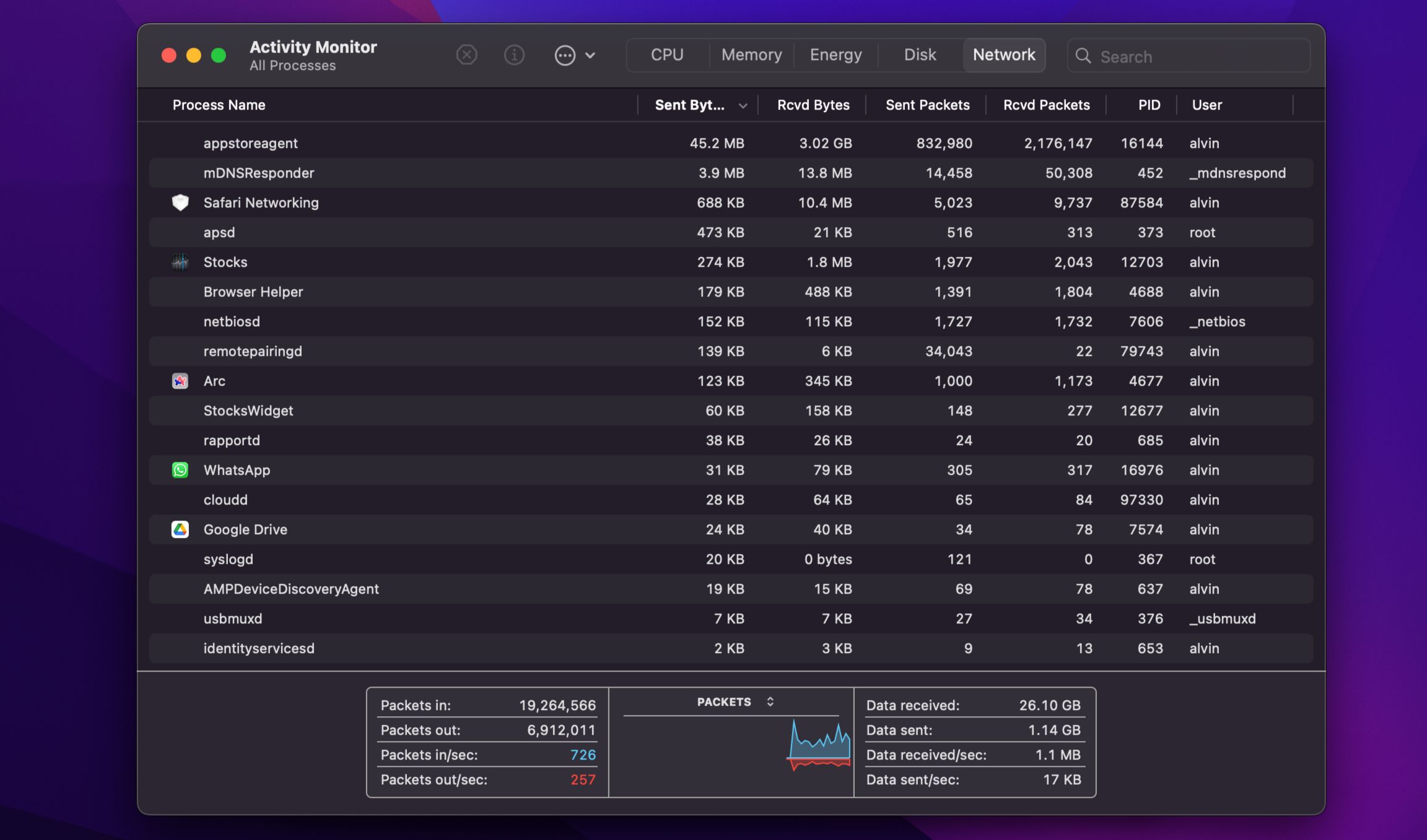
Check Network Activity
One unique feature of monitoring software is that it often sends data back to the owner, whether it’s your keystrokes, screenshots, audio recordings, or activity logs. This means it will frequently use your internet connection even when you’re not doing anything online.
Because of this, checking your laptop’s network activity can help you spot any unusual transfers indicative of spyware.
On Windows, search for Resource Monitor and select it from the search results. Once open, select the Network tab for a detailed breakdown of your network usage.
On macOS, open Activity Monitor and click on the Network tab.
While viewing network usage, look for unfamiliar processes or applications consistently sending or receiving data in the background. Frequent, unexplained spikes in network usage could be a red flag.
In addition to Resource Monitor and Activity Monitor, you can use third-party tools to monitor network activity on Linux, macOS, and Windows. On Windows, you can use GlassWire or NetBalancer. On macOS, LuLu is an excellent choice.
If you have concerns that someone is monitoring your computer but can’t see any obvious signs, review your system for unfamiliar apps, check your network traffic, and go through your startup programs and browser extensions. The best approach is to start with the easy methods and work down to more advanced techniques.



:max_bytes(150000):strip_icc()/twoku-twtich-roku-app-2053432b763a40d788ef726974d9ed2a.png?w=1174&resize=1174,862&ssl=1)




Leave a Comment
Your email address will not be published. Required fields are marked *