Do you install a lot of different apps on your Linux computer? Are you worried that one of these apps might have a virus or malicious code that steals your data? Well, here are five security practices I personally follow to keep my Linux PC safe from these threats.
Linux is a reasonably secure operating system, but it’s not virus-free. This is especially true for someone like me who installs and reviews different apps and software. My security risks are higher as I can accidentally install something with sudo privileges that ends up compromising my system. Thankfully, with nearly a decade’s experience in testing new software, I’ve developed a system to keep my Linux PC ultra-secure and virus-free.

Related
This Linux Distro Is Focused on Maximum Privacy and Anonymity, Here’s How to Use It
Protect your privacy with Tails.
5
Monitor Your Network Activity
One of my biggest security concerns is my data being stolen from my system. As a tech writer, I constantly install different apps and tools on my PC, and I would hate it if one of them had some malicious inclinations and decided to phone home sensitive data from my system.
To protect myself from these types of mishaps, I use Portmaster by Safing. It’s a free and open-source (FOSS) network activity monitor and application firewall. I can use it to check which apps are currently accessing the internet, what servers they are connecting to, as well as how much data they are uploading and downloading. I can also use it to block an app from accessing the internet altogether.
For example, take a simple calculator app I might have downloaded. Portmaster can tell me if it’s connecting to the internet, which is strange! But at the same time, it can also tell me if it’s uploading data—which is concerning, versus downloading data—which is understandable, especially for currency conversion tasks! So, while a calculator app accessing the internet is worrisome, Portmaster helps me understand what it’s doing, and make an informed decision instead of being paranoid.
Of course, you could simply use the terminal to get network-level control over your apps, but Portmaster makes it easier through an elegant and modern graphical interface.
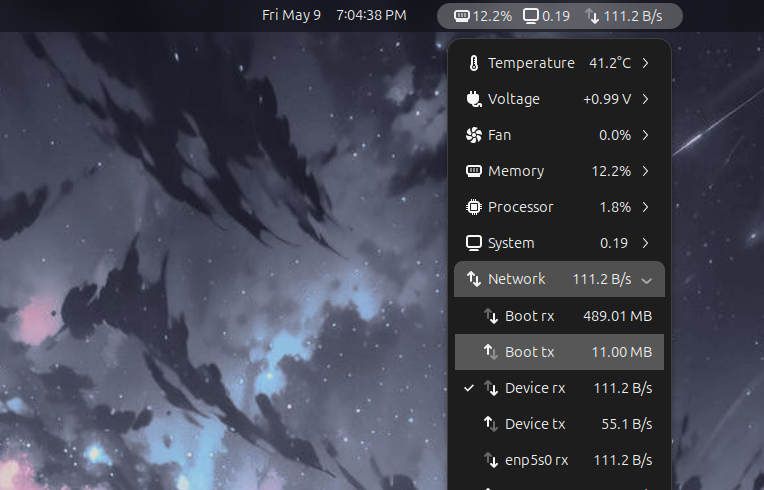
Now, apart from Portmaster, I also use taskbar widgets to keep an eye on overall network traffic all the time. I personally use the KDE Plasma desktop environment and the Network Monitor widget. But if you’re on GNOME, you can use the Vitals GNOME extension and get the same functionality.
The idea here is to get a quick view of the current network traffic. I generally have an idea of what normal network activity looks like—download spikes during browsing, upload spikes during, well, uploading stuff. If I notice significant network activity when I’m idle or just typing in a text editor, I instantly know something’s amiss and that it’s time to visit Portmaster to find out what’s wrong.
While a network monitor can help you check if apps are stealing data from your system, it can’t protect you from installing a malicious app in the first place. This is why I prioritize downloading apps from my distro’s official repository (repo). These packages are vetted by the distro’s maintainers and then made available to the you. As such, if you trust your distro, there’s no reason to question the apps it’s distributing.
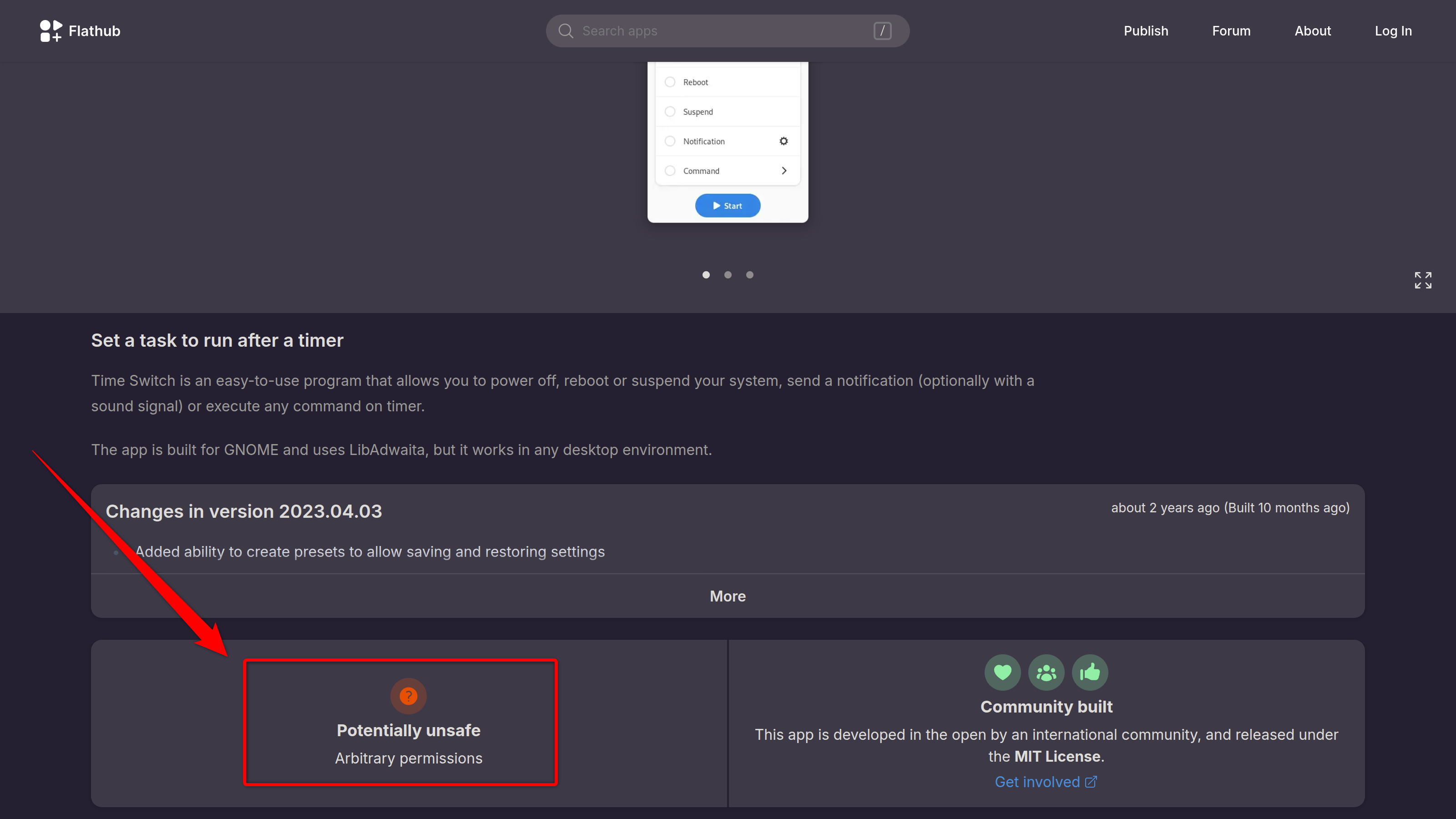
That said, not all apps are always available in the official repos. This is when I look into containerized options like Flatpak. These apps run in a sandbox, making them generally safe to use, but don’t trust them blindly. Some apps request broad system access, which can pose security risks. Therefore, always check the permissions of an app before installing, see if those are actually necessary for it, and then press the Install button. For Flatpaks, you can generally check the Flathub website to see its security rating.
Sometimes I also need to download stuff from third-party repos like PPAs (Personal Package Archives) and the AUR (Arch User Repository). Here I follow a simple rule of thumb: popularity equals scrutiny. If thousands of users install an app from the AUR, there’s a lot of eyes on it to check for potential malicious code. That said, if you don’t know about the popularity of the app, you can simply search for it on Reddit, or your distro’s official forum and check what others have to say.
The tricky part is when you need to install some random script or tool, e.g., desktop widgets or custom themes from GitHub. This is where I check how many people are watching the project and how many stars it has. Usually something in the thousands or upper hundreds is enough to give me confidence, as most of these people are developers looking into the code and not regular users.

Related
GitHub is the Best Place for Free and Open Source Software
GitHub contains almost every kind of software, completely for free. But navigating it is tough, so where do you start?
If it’s a small script with a couple of hundred lines of code, you can potentially do a security audit yourself. You can use Gemini 2.5 Pro (known to be good at coding) to audit the app for you. Simply open the GitHub page for the script, and in the URL, change github to uithub. This will show you the full repository structure and code context which you can now copy and paste into Gemini 2.5 Pro and ask it for an audit. For example, this URL:
Becomes:
AI and LLMs are still prone to making mistakes and hallucinating. As such, don’t blindly trust what AI tells you about the code. If it flags something, consult a professional about it before deciding what to do.
3
Routinely Audit Installed Apps
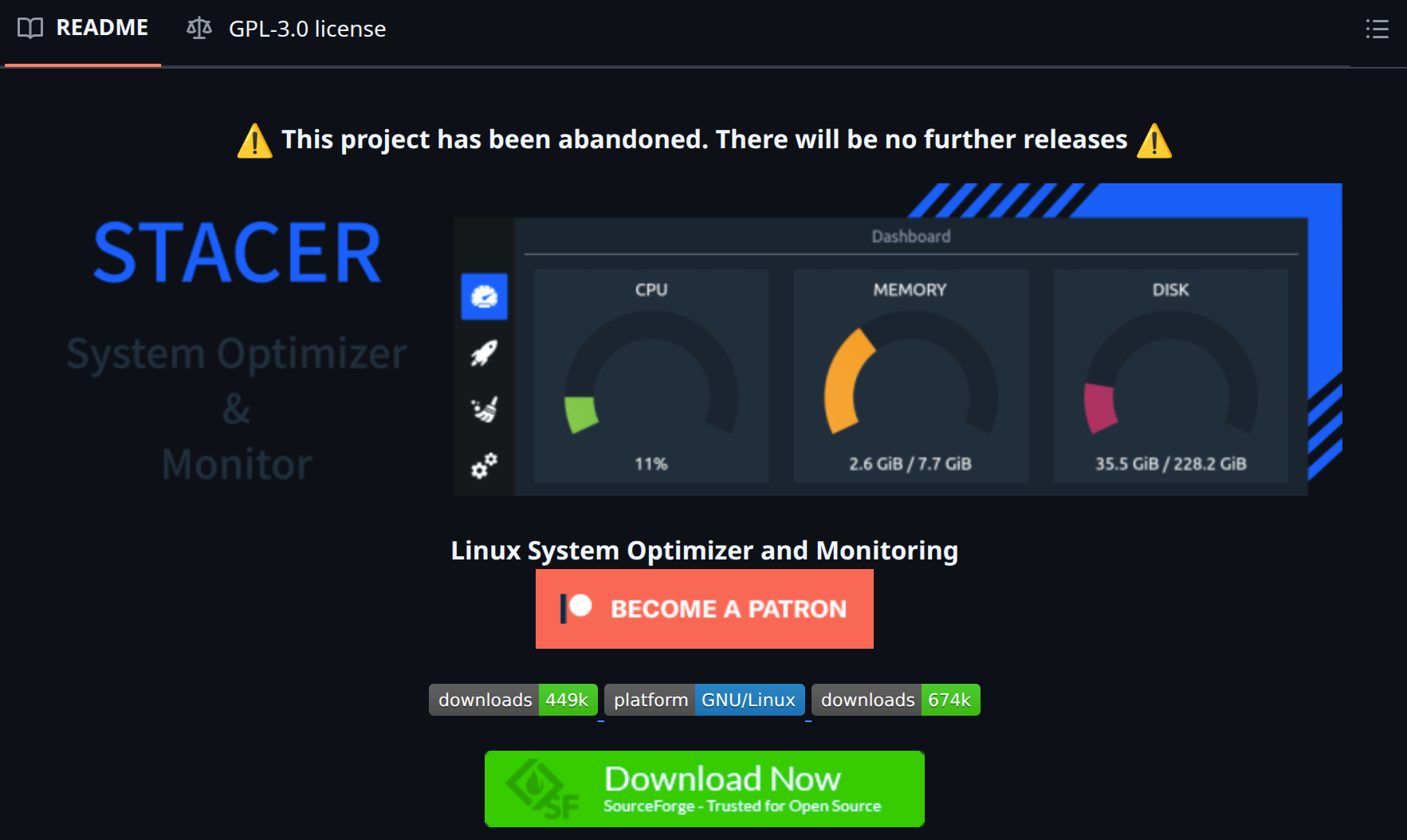
Here’s a trap I’ve fallen into before: assuming that once-secure software stays secure forever. I was a huge fan of the Stacer system monitor app. It comes with a sleek and modern UI and provides comprehensive system stats. However, until recently, I didn’t know that the app was officially in an abandoned state for the past two years.
This matters because abandoned software doesn’t get security patches. If someone discovers a vulnerability tomorrow, there’s no developer to fix it. I reluctantly removed Stacer from my system despite it working perfectly fine.
Now, if you don’t want to make the same mistake that I did, consider setting up Google Alerts for every single app you use. This way, whenever there is any news about those apps—whether it be new updates or security vulnerabilities—you’ll know right away, and then you can quickly download the security patch the developers might have issued or uninstall the app until they do.
This is why most security veterans encourage keeping a few essential apps and uninstalling the ones you don’t use anymore. Each application expands your attack surface, and micromanaging everything can become a huge chore.
Related
Why Are There So Many Zero-Day Security Holes?
Why do these vulnerabilities keep appearing? The answer is nuanced.
2
Enable 2FA for Your Desktop
This security trick isn’t widely known, but you can actually enable two-factor authentication on your Linux system, similar to how you secure your online accounts. I implemented this because I have a practical problem—the password I use for my user account isn’t particularly strong. Since I have to type it frequently, I use memorable phrases rather than complex 64-character-long alphanumeric strings.
Now, by setting up 2FA for my distro, I’ve added an extra security layer to compensate for my weak password without making it impossible to remember. This way, even if someone guesses my password, they still can’t access my system without the physical device that generates my authentication codes.
That said, it can be somewhat inconvenient to enter a verification code every time you log in or use sudo in the terminal, so I wouldn’t recommend this to everyone. In fact, most of the security tips you try to employ come at some cost to your overall convenience, and I’ve personally decided I’m okay with this.
1
Take Regular System Backups
While some attacks aim to steal your data, others want to destroy it or hold it hostage through ransomware. Your best defense against the latter is a solid backup strategy. I maintain an automated backup system that regularly copies my essential files to the cloud. If you don’t want to save it in the cloud, you can also save it to an external drive or a Network Attached Storage (NAS).

Related
How To Prepare For and Fight a Ransomware Attack
Ransomware is devastating, expensive, and on the rise.
A key point is not to keep the backup of your system on the system itself. This ensures that if my main system is compromised, my backups remain safe. I’ve seen too many people keep their backups on the same system they’re backing up. This completely misses the point—if your system is compromised or crashes, those backups go down with it.
And there you have it, the top five things I do to keep my Linux PC safe from viruses, hacks, and security threats. Feel free to replicate any of these security measures into your own workflow. That said, if you want the absolute necessary tips and tricks, check out our beginner’s guide to basic Ubuntu security.







Leave a Comment
Your email address will not be published. Required fields are marked *