I love the idea that my computer is free from spyware, and who doesn’t? Who likes the idea of someone stealing their secrets? For me, the benefits of Qubes are indispensable and drastically outweigh its challenges.
A Read-Only File System Gives Me Peace of Mind
Qubes consists of virtual machines, aka AppVMs. It protects the root file system of these AppVMs from permanent changes. It resets system changes when I reboot the AppVM—peace of mind. What is a virtual machine? A virtual machine is a piece of software that simulates hardware environments; one can then install operating systems into it.
AppVMs are based on templates, aka TemplateVMs. The TemplateVMs provide the root file system, and AppVMs provide the user files. Together they provide a complete system.
Unless I keep a close watch on my system, I can’t truly know what may lurk in the depths after prolonged use. Rootkits are sophisticated software, and they do a good job at hiding malware. It requires specialist skills to remove such malware, and so most people choose to reinstall their system instead.
To get a clean system, I restart my AppVM. If malware persists in user files, then I recreate the AppVM. Both approaches take seconds. I only need to install and configure a TemplateVM once.
Related
7 Ways to Spot an Impostor Website
Don’t let scammers steal your information.
Thoroughly Testing Software Without Full Commitment
I often test out software on my system, changing configuration files and starting and stopping services. This approach creates a mess, and it changes how my system functions while I’m using it. Suppose I am testing out a new DNS service but need to check a website; on standard Linux, my DNS requests may go unanswered.
On Qubes, I use a disposable VM (DispVM), a special AppVM that wipes all changes upon restart, including user files. I boot up the DispVM, install the software, configure it, and use it. I then realize that it’s not great and simply close the active window. Qubes then shuts down the DispVM and resets all changes for me. I can essentially modify any system file, knowing that it does not corrupt my system or affect my workflow.
A Leak-Proof VPN to Preserve My Privacy
VPNs are pretty popular these days, and most people use them for the same reason: privacy. However, if my VPN goes down, my traffic leaks onto the open internet, which is not good for privacy.

Related
The Best Budget VPNs of 2025
VPNs can be pricey; these five services offer great value all year round for those that don’t want to spend that much.
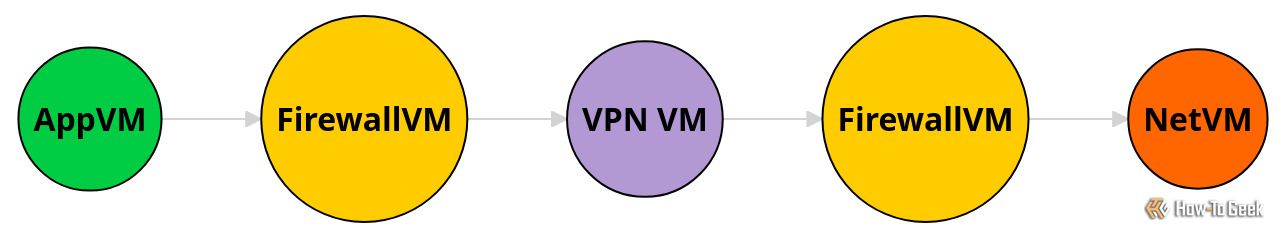
Networking on Qubes consists of a chain of virtual machines (VMs). The traffic flows from an AppVM, through a FirewallVM, and out through a NetVM. If I add a VPN VM, I will sandwich it between 2 FirewallVMs. One firewall protects my system; the other ensures traffic only goes to the chosen VPN server.
On a normal Linux distro, I could achieve a similar outcome with firewall rules. But on Qubes, I can run multiple VPN VMs together and even give some AppVMs direct access to the internet.
Not only do I get the flexibility to connect to multiple VPN services, but I also get robust security sandboxes provided by Qubes. With the firewalls in place, my connections act exactly as I expect, which gives me confidence my traffic does not leak.
Disposable VMs Protect My Secrets
Passwords are secrets, and in a digital world, everyone has passwords, sometimes too many. On standard Linux, you trust that your system is clean; on Qubes, I know that my system is clean.

Related
The Best Password Managers of 2025
Using a password manager will make your personal information more secure, but which are the best?
One of the most alluring features of Qubes is the DispVM. It’s perfect for high-risk and sensitive VMs.
- High-risk VMs: VMs exposed to untrusted environments, like a NetVM or VPN VM.
- Sensitive VMs: VMs that manage secrets, like a banking or email VM.
When I start these VMs, I know they start with a clean slate; when I shut them down, they discard everything (including my login sessions). If you pair DispVMs with a hardware security key, your secrets become juice that’s not worth the squeeze.
The Flexibility to Run Multiple Distros
On standard Linux, I can run different distros in virtual machines, but I still have to navigate a clunky embedded desktop environment. On the other hand, Qubes wraps applications to make them feel like normal desktop applications. I can move freely between applications, across multiple distros, like it’s one seamless desktop. It’s a feature unique to Qubes.
For each distro that you use, follow sensible practices to secure your system and data—even on Qubes.
Protect Myself From Random People on Public Wi-Fi
When you use public Wi-Fi, you expose yourself to unknown risks. Attacks on a Wi-Fi card’s drivers or firmware are possible. A compromised device has unrestricted access to memory.
Internal devices, such as a WiFi card, are PCI devices. Qubes wraps PCI devices up in a dedicated VM, using a technology called IOMMU. If compromised, a wrapped device can only attack its assigned VM.
Qubes wraps my publicly exposed Wi-Fi card with a NetVM by default. Because it’s a DispVM, Qubes discards any malicious changes upon reboot. What’s more, my NetVM sees only VPN traffic, and a FirewallVM prevents further attempts to penetrate my system.
The described setup is not easy to achieve on standard Linux, and it requires considerable technical knowledge.
Isolating Untrustworthy USBs Keeps My System Safe
Plugging a USB device into a computer is risky. A malicious USB has multiple options to compromise my system. For example, they can emulate a keyboard device and enter crafted keystrokes; they can exploit driver bugs and attack the OS itself.
Like the NetVM, it’s best to assign USBs to a dedicated (and empty) VM. To do this, I assign the associated PCI devices to it. Now when I plug in a USB device, I have confidence that an attack is completely useless. A quick reboot, and it’s gone.
Qubes is indispensable to me, and after a short time on standard Linux, I’m paranoid about what I have picked up along the way. On Windows, I had the false sense of security that an antivirus brought, but on Linux, it’s not really an outstanding option. In contrast, the Qubes approach is like save points in a video game; I start from a trusted state every time.
Qubes is stable and ready for prime time, but it requires at least 16 GB of RAM and other crucial technologies (VT-x, VT-d, and SLAT). If you’re interested, you should start with the Hardware Compatibility List, ask questions on the Qubes forum, and head over to the Qubes Installation Guide. However, beware that Qubes is challenging.







Leave a Comment
Your email address will not be published. Required fields are marked *