Every morning, we scan through dozens of emails, but unknowingly put our security at risk. Those seemingly harmless clicks and routine habits developed over years of email use are exactly what cybercriminals count on to succeed with their attacks.
4
Shortened URLs Hide Dangerous Destinations
Shortened URLs look innocent enough, and those tiny bit.ly and tinyurl.com links save space and look cleaner. But the problem is that you can’t see where they actually lead until it’s too late.
Cybercriminals love URL shorteners because they effectively mask malicious websites. That “helpful” link claiming to verify your account could redirect you to a convincing fake login page designed to steal your credentials.
Most email clients don’t preview shortened URLs, leaving you completely blind to the destination. Even hovering over these links often shows nothing more than the link shortener’s domain, not the actual target site.
Before clicking any shortened link, expand it first. You can use a URL checker to reveal the true destination safely. Once you find out the long URL, scan it with VirusTotal or URLVoid for any red flags. These simple steps can save you from phishing attempts and malware downloads.
When in doubt, the safest approach is to navigate to the website directly instead of clicking the link. Most legitimate companies include their full website address in emails anyway. If you still receive suspicious emails regularly, consider implementing rules to block phishing emails from your inbox entirely.
Some URL shorteners offer preview features, but don’t rely on them completely, as determined attackers can work around these protections.
3
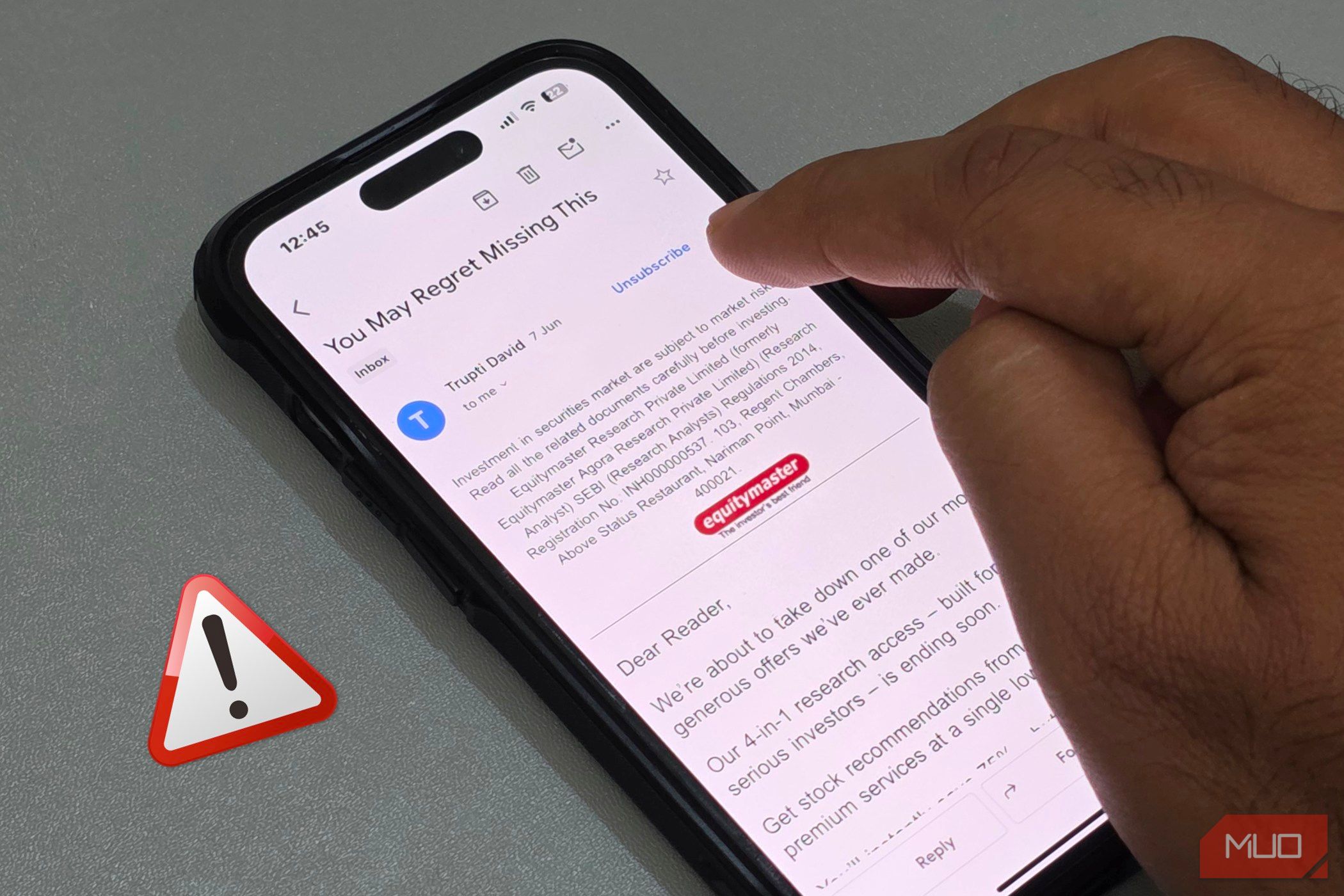
“Unsubscribe” Links Can Confirm You’re a Real Target
In some spam emails, the Unsubscribe button at the bottom can often be a trap. Legitimate companies honor unsubscribe requests, but scammers use these clicks to confirm your email address is active and monitored. The moment you click, they know they’ve found a real person, and your address gets flagged as valuable.
This confirmation makes your email worth more on the dark web. Verified active addresses sell for higher prices to other cybercriminals, meaning more spam, phishing attempts, and potential security threats heading your way.

Related
I Tried a Dark Web Monitoring Service—Here’s What I Found Out
Your data might be on the dark web. Mine was.
Some unsubscribe links not only confirm your address but also redirect to malicious websites or automatically download malware onto your device. So, if you’re drowning in unwanted emails, don’t click Unsubscribe, but mark the emails as spam and block the sender.
Trust your instincts—if an email feels suspicious, those unsubscribe links probably aren’t there to help you. For the legitimate newsletters you signed up for, there are safer ways to unsubscribe from newsletters in Gmail that don’t put you at risk.
2
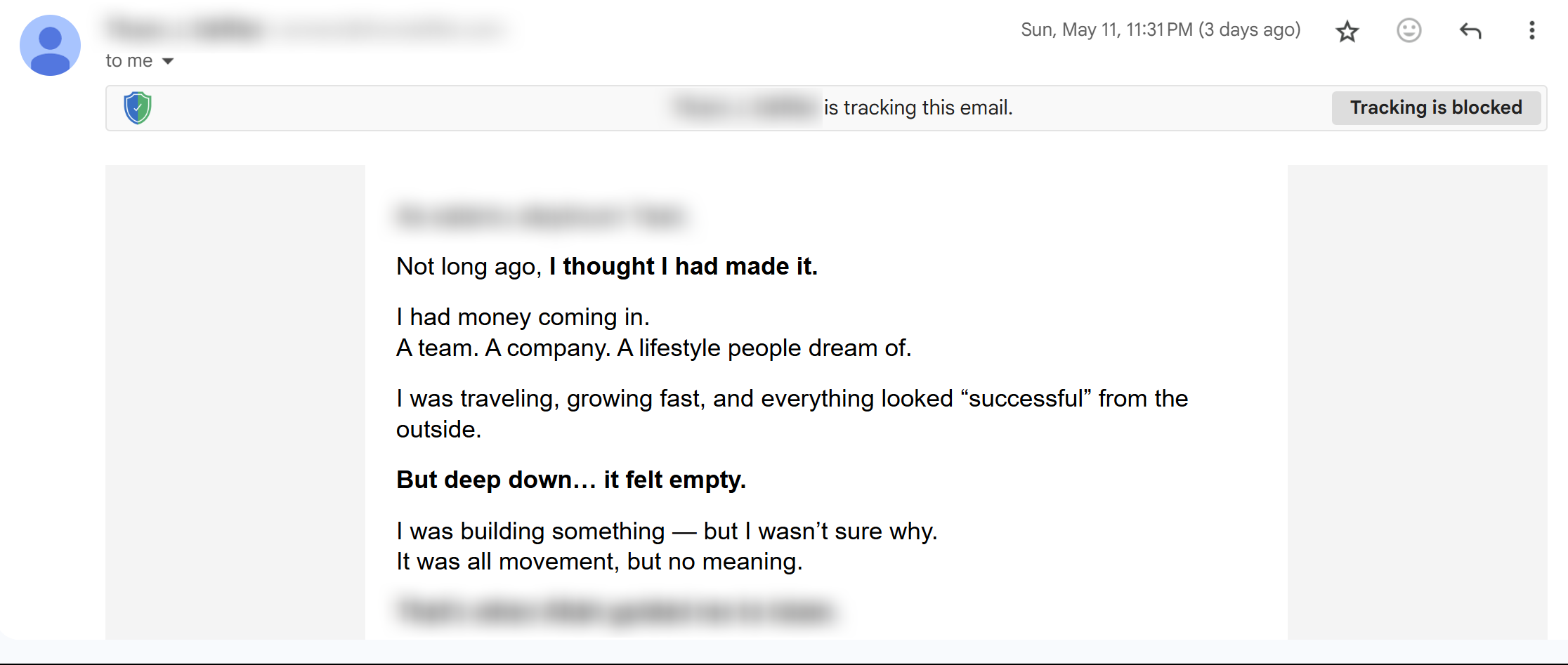
Auto-Loaded Images Give Away More Than You Think
Most email clients automatically load images when you open messages. That seems harmless, but it isn’t.
Senders embed tiny 1-pixel-by-1-pixel email tracking pixels within those images, which report back to senders the moment they load. These pixels can reveal when you opened the email, what device you used, your approximate location, and even your IP address.
Marketing companies use this data to build detailed profiles about your habits. But cybercriminals exploit the same technology for more sinister purposes, such as confirming active targets and gathering intelligence for future attacks.
Some malicious images go beyond tracking. They can exploit vulnerabilities in image processing software or redirect to dangerous websites when clicked.
If you want convenience without compromise, browser extensions like Email Privacy Protector can block tracking pixels while still displaying images. However, I also use other easy methods to block email tracking pixels entirely.
There are some trade-offs between convenience and privacy, but knowing what’s happening behind those automatically loaded images helps you make informed decisions.
1
Document Attachments Need Verification First
Email attachments are cybercriminals’ preferred method of delivering malware, and they’ve become increasingly sophisticated in disguising threats. That “invoice.pdf” might actually be “invoice.pdf.exe”—a malicious executable masquerading as a document. These double extensions exploit Windows’ default setting of hiding file extensions, making dangerous files appear harmless at first glance.
Even legitimate-looking file types can harbor threats. Cybercriminals often use EXE and PDF file types to hide viruses, turning everyday documents into Trojan horses that install malware when opened.

Related
6 Easy Ways to Check If a Downloaded File Is Safe Before Using It
Your downloaded file could be malware—but there are some easy ways to check.
Don’t forget to verify any attachment that seems suspicious before opening it. Verify the sender through a separate communication channel if you can. Additionally, you should run a virus scan to spot and avoid malicious attachments.
Check file types carefully by enabling file extensions in Windows so you can spot suspicious double extensions. I always try to be wary of executable files (.exe, .bat, .scr) and macro-enabled documents (.docm, .xlsm) from unknown sources.
When in doubt, upload suspicious attachments to online virus scanners before opening them locally. Your antivirus software provides an additional layer of protection, but human vigilance remains the strongest defense against attachment-based attacks.
Email security doesn’t require paranoia; it just requires awareness. These seemingly innocent habits have tricked millions of people, but recognizing them puts you ahead of most. Take a moment to think before you click, and those split-second decisions will protect you from cyber threats.



:max_bytes(150000):strip_icc()/LEDEAmazonPrimeDaysJuly2025-bd1d286439d64552821ac7571c7007f4.jpg?w=1174&resize=1174,862&ssl=1)




Leave a Comment
Your email address will not be published. Required fields are marked *