The dark web gets a bad reputation, but I’ve learned to navigate it safely for legitimate research and privacy purposes—without breaking any laws.
How to Access the Dark Web Safely
I always start my dark web journey with the right security setup. The first thing I do is download the Tor browser directly from the official Tor Project website. I never trust third-party download sites because they might bundle malicious software with the browser. This step alone protects me from countless security risks.
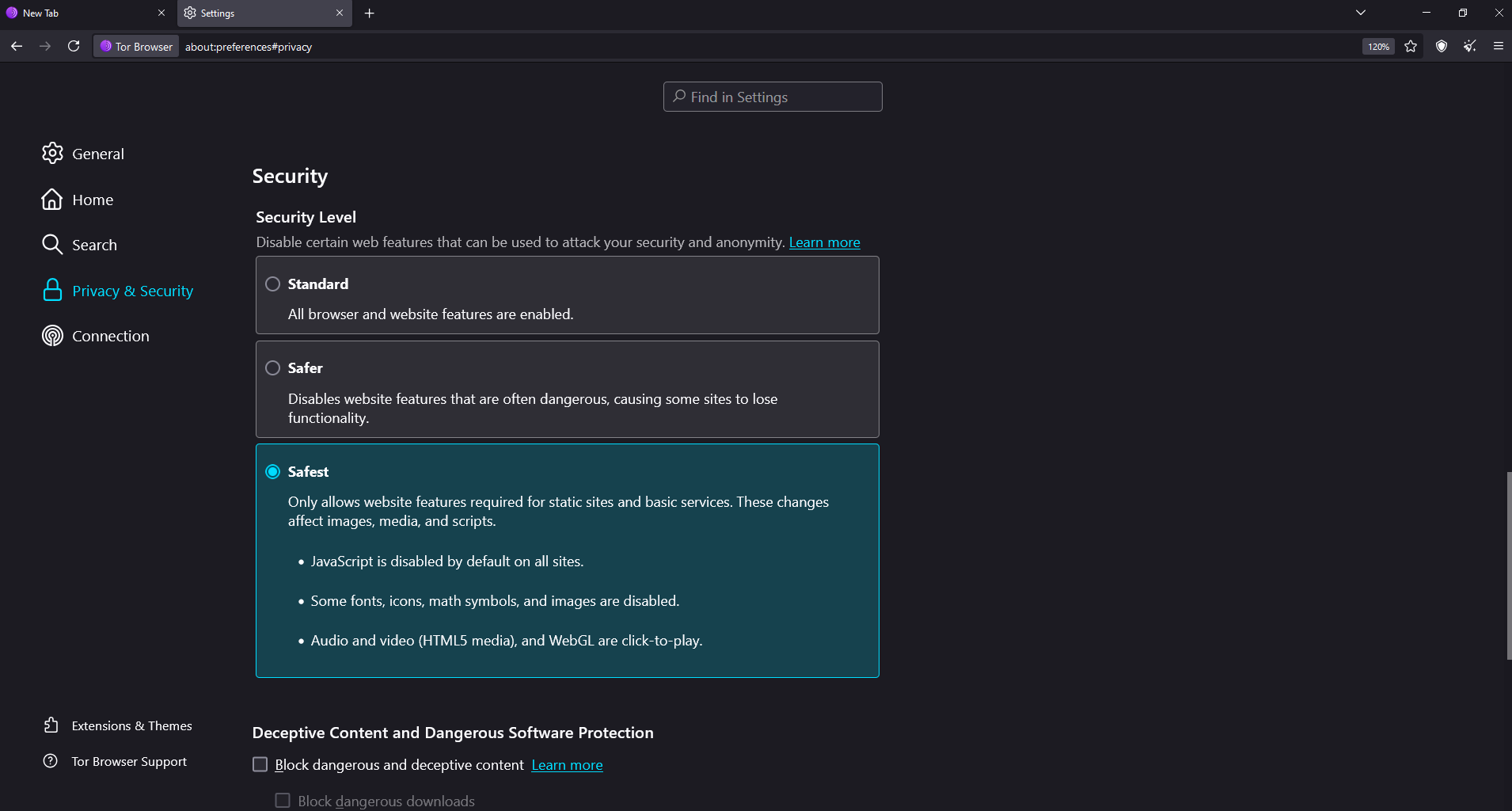
My security setup includes adjusting Tor’s built-in security settings. I change the security level from Standard to Safer or Safest depending on what I’m doing. The Safer setting disables potentially dangerous website features, like certain fonts and math symbols, while Safest blocks JavaScript entirely. JavaScript can leak sensitive information, so I disable it when browsing unfamiliar sites.
Many people recommend using a VPN service, as it creates an extra layer of protection from your ISP. I personally don’t bother, since I don’t visit the dark web as much as I used to, and paying for a VPN just to access onion sites isn’t worth the monthly subscription. I also refuse to use free VPNs, as they are known to rent your IP address to other users or sell your data. Using Tor in itself already provides pretty good protection by encrypting your data and creating a secure tunnel for your connection. There are different ways a VPN can be useful, but its utility is limited if you’re only visiting the dark web.
If I were to need some extra layer of protection, I would sandbox my activity using privacy-focused operating systems (OS). If you primarily use Windows, I recommend using Whonix. This OS can run on top of your Windows desktop using free virtual machine software, such as VirtualBox. What I like about Whonix is that it’s lightweight, easier to set up than Tails OS, and sandboxes your entire Tor session. So, even if you accidentally download something from the dark web (which you shouldn’t!), the virus can only spread inside the Whonix OS. Just make sure to keep everything at default settings unless you know what you’re doing.
The dark web runs slower than regular internet browsing because my traffic bounces through multiple nodes across the globe. I expect delays and don’t get frustrated when pages take longer to load. This slower speed actually indicates that the security features are working properly.
Navigating Through the Onion Network
Understanding how onion routing works helps me navigate the dark web more effectively. The technology encrypts data in multiple layers, like an onion, and sends it through several volunteer-operated servers, known as nodes. Each node peels away one encryption layer to reveal the next destination, but no single node knows both where my traffic started and where it’s going.
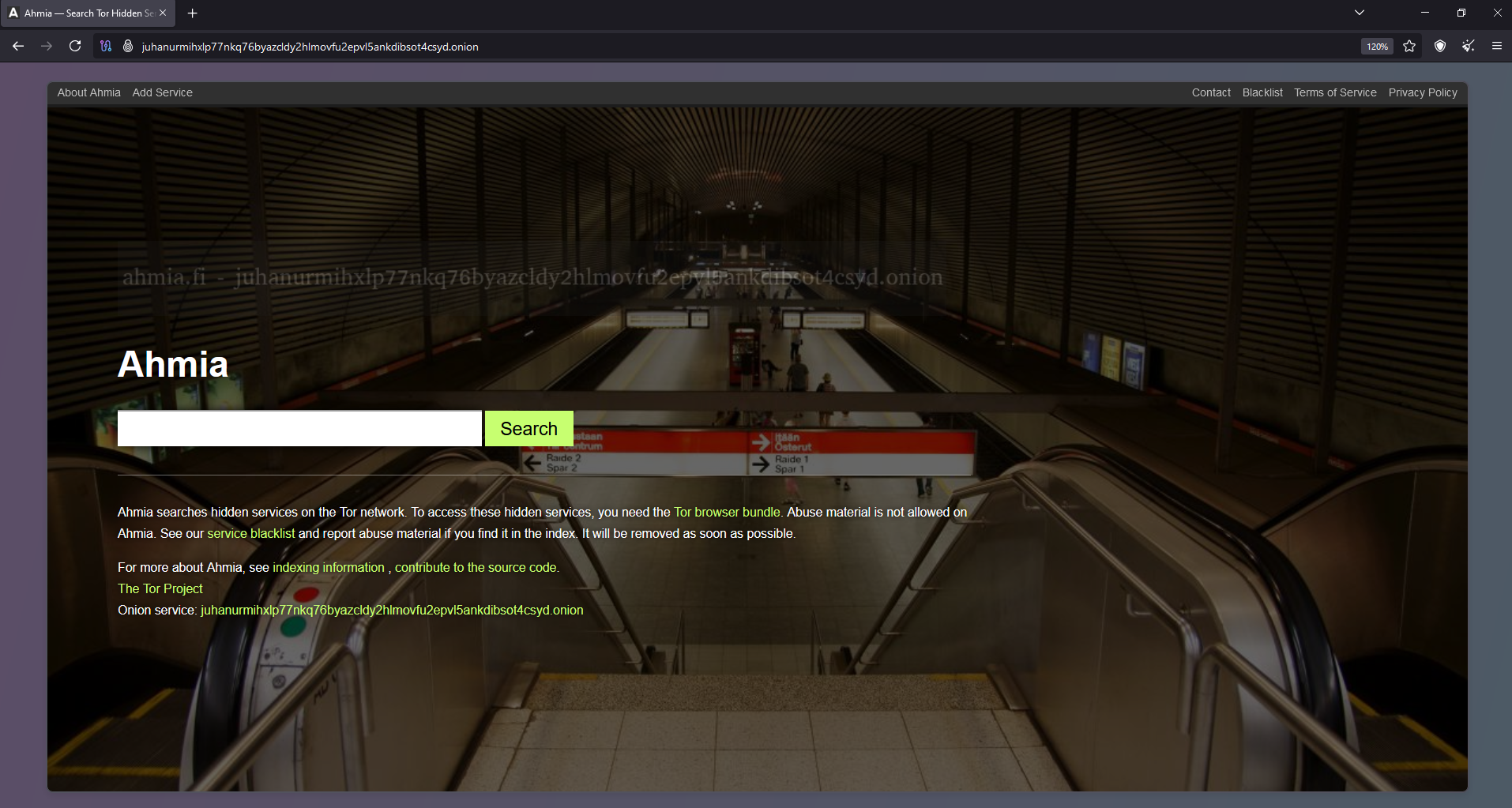
When I access onion websites, I use specific search engines designed for the dark web. DuckDuckGo serves as Tor’s default search engine. But I choose to use search engines like Ahmia.fi to help me find legitimate sites while filtering out illegal ones.

Related
The 12 Best Deep Search Engines to Explore the Invisible Web
Google and Bing can’t search for everything. To explore the invisible web, you need to use these special deep search engines.
I always verify onion URLs carefully before visiting them. Phishing sites often create addresses that resemble legitimate ones with subtle changes. I bookmark trusted sites and use well-known directories to find new ones rather than clicking random links.
Onion services can host any type of content, not just websites. Some provide secure chat services, file sharing, or other applications that benefit from anonymity. Major legitimate organizations like Facebook, The New York Times, and The Guardian maintain onion versions of their websites for users in countries with internet censorship.
While there are more advanced web crawlers on the dark web, I still stick to known search engines to ensure I only visit legitimate sites and services.
My Rules When Browsing the Dark Web
To keep myself safe, I follow a few rules to ensure I don’t accidentally do anything illegal while browsing the dark web.
- Never share personal information: I don’t use my real name, email address, phone number, or any identifying details. If a site requires registration, I create fake credentials and use secure email services like ProtonMail.
- Avoid downloading files: Downloads are one of the biggest malware risks. Cybercriminals often disguise malicious software as legitimate files. If I absolutely need to download something for research, I only do it inside Whonix or Qubes OS.
- Follow a strict “look but don’t touch” policy: If I see anything questionable or illegal, I leave immediately and never return. I don’t click on suspicious links, never try to buy anything, and skip marketplaces altogether—even if they claim to be legit. I’ve checked out plenty, and the prices are usually too good to be true.
- Never use the dark web for financial transactions: Even though cryptocurrencies offer some anonymity, I avoid anything involving money. This rule keeps me from being tempted to buy illegal stuff and protects my financial info.
- Limit my browsing time: I don’t wander aimlessly. I go in with a specific research goal, finish quickly, and log out. This focused approach lowers my chances of running into dangerous content.
Sticking to these rules keeps my dark web sessions focused, safe, and drama-free. If you treat every visit with caution and discipline, you’ll avoid most of the trouble that catches less careful explorers.
Dark Web Red Flags I Avoid
So, how exactly do I tell if a site is illegal, a scam, or trying to hack me? Experience has taught me to recognize several red flags that signal dangerous or illegal activity on the dark web. The biggest warning sign is any site offering illegal goods or services. I immediately leave sites that advertise drugs, weapons, stolen data, illegal services, or counterfeit documents.
Forums or chat rooms discussing specific methods for committing crimes represent another major red flag. I don’t participate in conversations about hacking techniques, fraud methods, or other illegal activities. Even reading such content could potentially implicate me in criminal activity.
I’m wary of sites that aggressively request personal information or try to install software on my device. Legitimate dark web sites typically respect user privacy and don’t push downloads or ask for identifying details. Sites that behave otherwise likely have malicious intentions.
Any site offering “too good to be true” deals or services raises immediate red flags. Scammers operate extensively on the dark web, targeting users who think they can get expensive items cheaply or access exclusive services. I remember that if something seems impossible, it probably is.
I avoid sites with lots of pop-ups, aggressive advertising, or poor design quality. Professional organizations that maintain dark web presences typically create clean, functional sites similar to their regular websites. Sloppy design often indicates either scam sites or places where security isn’t a priority.
The dark web ultimately represents a tool that can serve both good and evil purposes. Like any powerful technology, its value depends entirely on how people choose to use it. By following proper security practices and maintaining ethical standards, you can safely explore the dark web without accidentally doing something illegal.







Leave a Comment
Your email address will not be published. Required fields are marked *